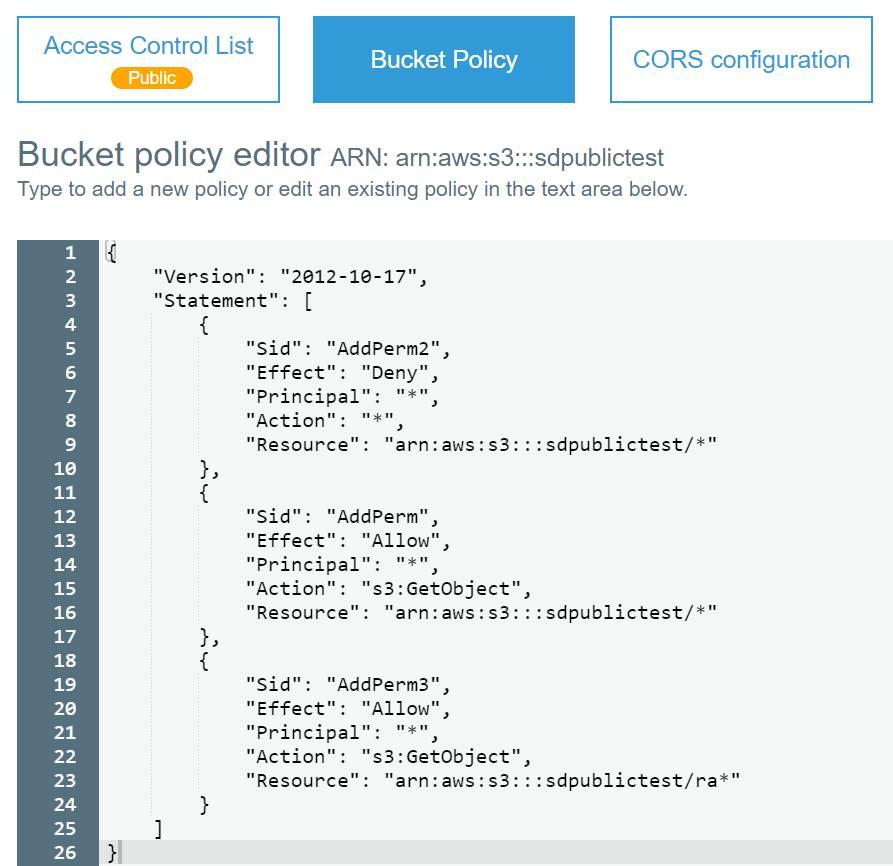
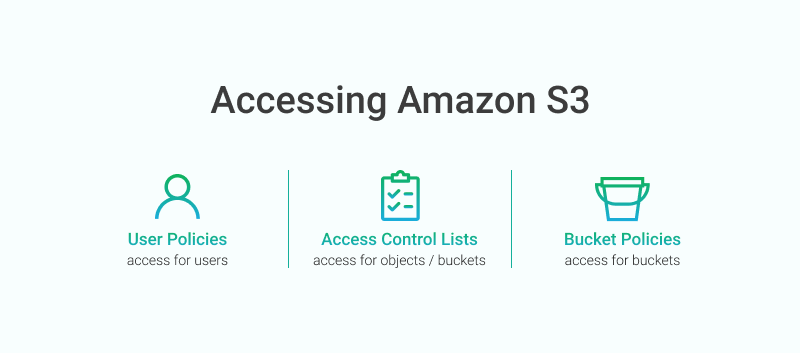
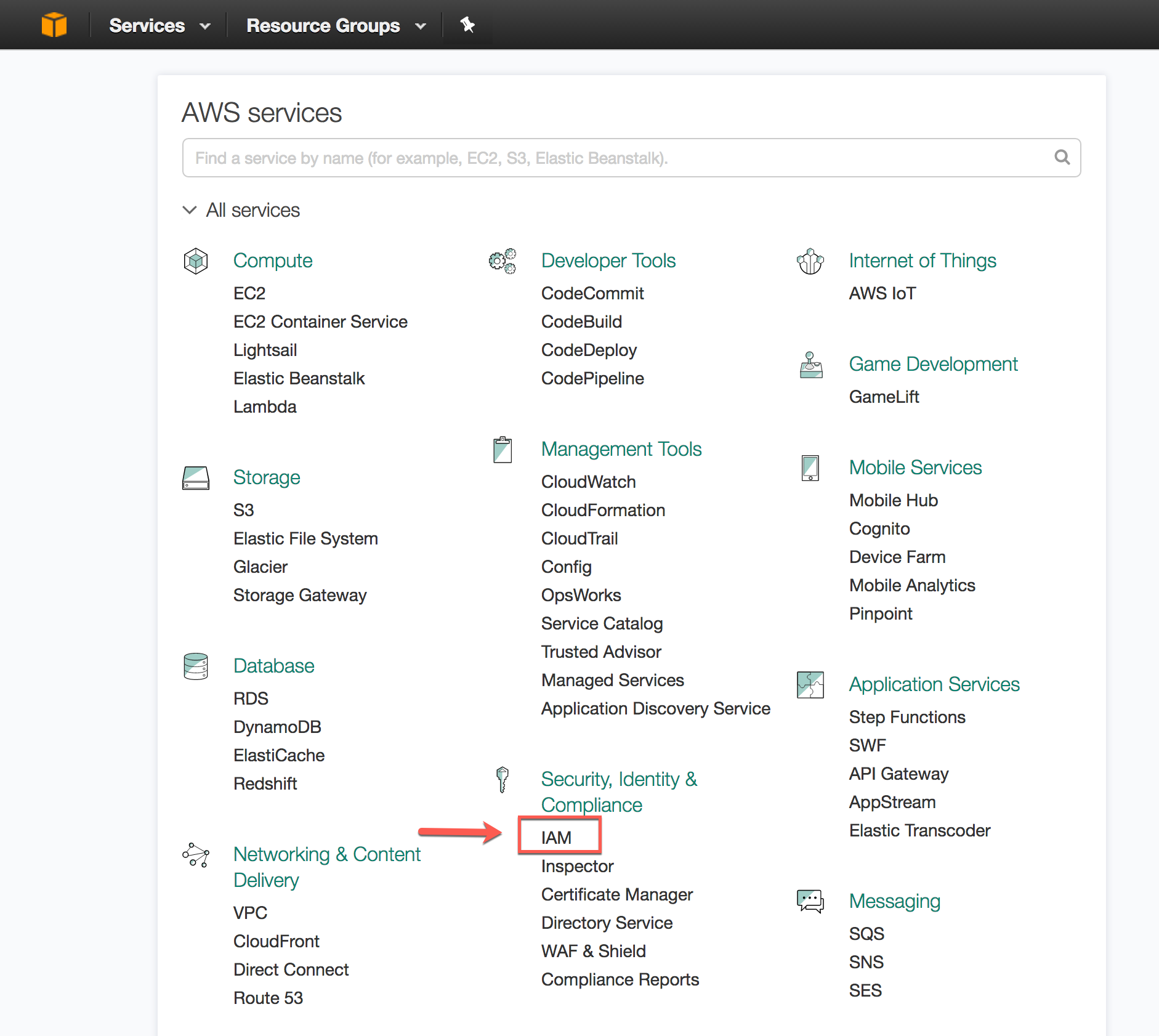
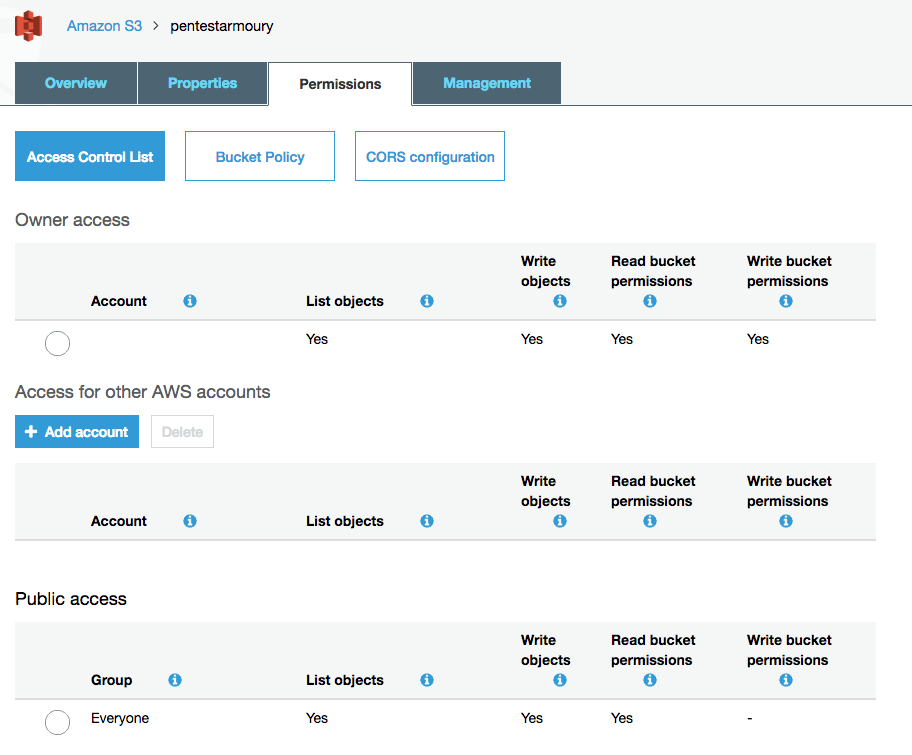
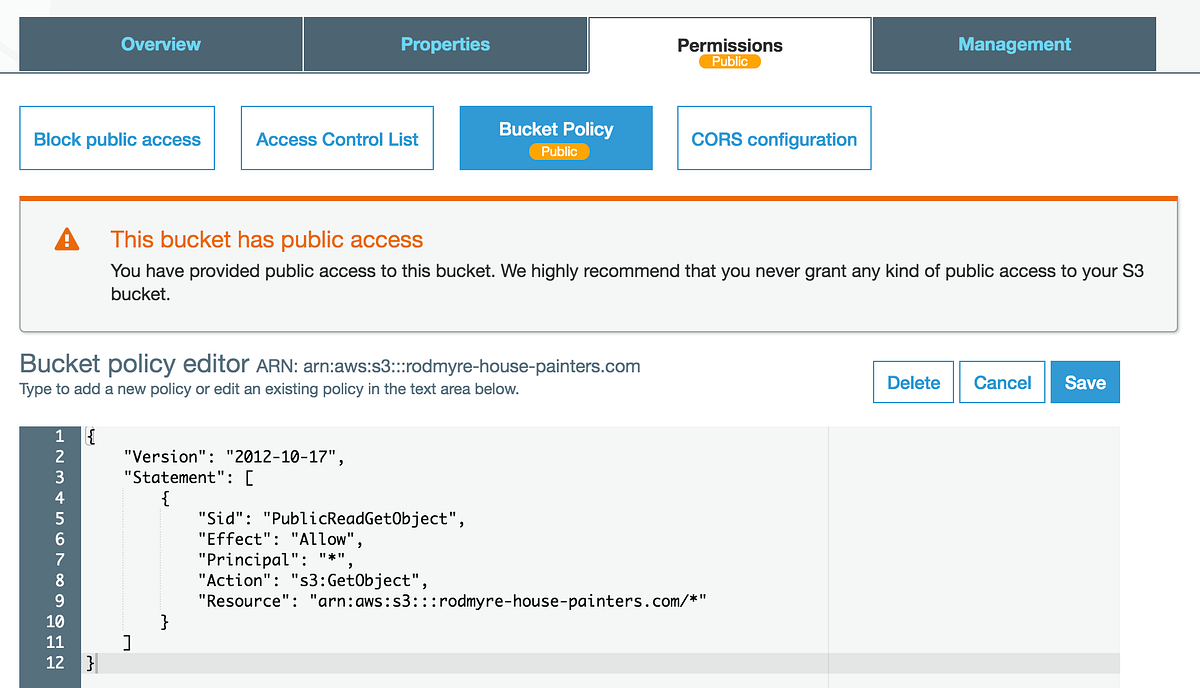
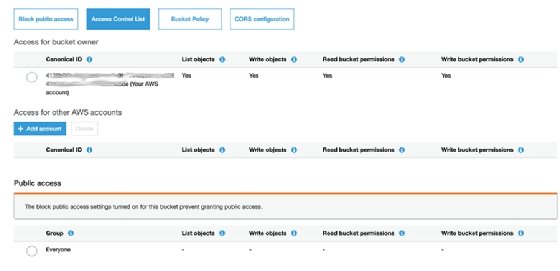
Sample S3 Bucket Policies. [Allowing only SSE-KMS based encrypted… | by Crishantha Nanayakkara | Medium

AWS has new tool for those leaky S3 buckets so, yeah, you might need to reconfigure a few things • The Register

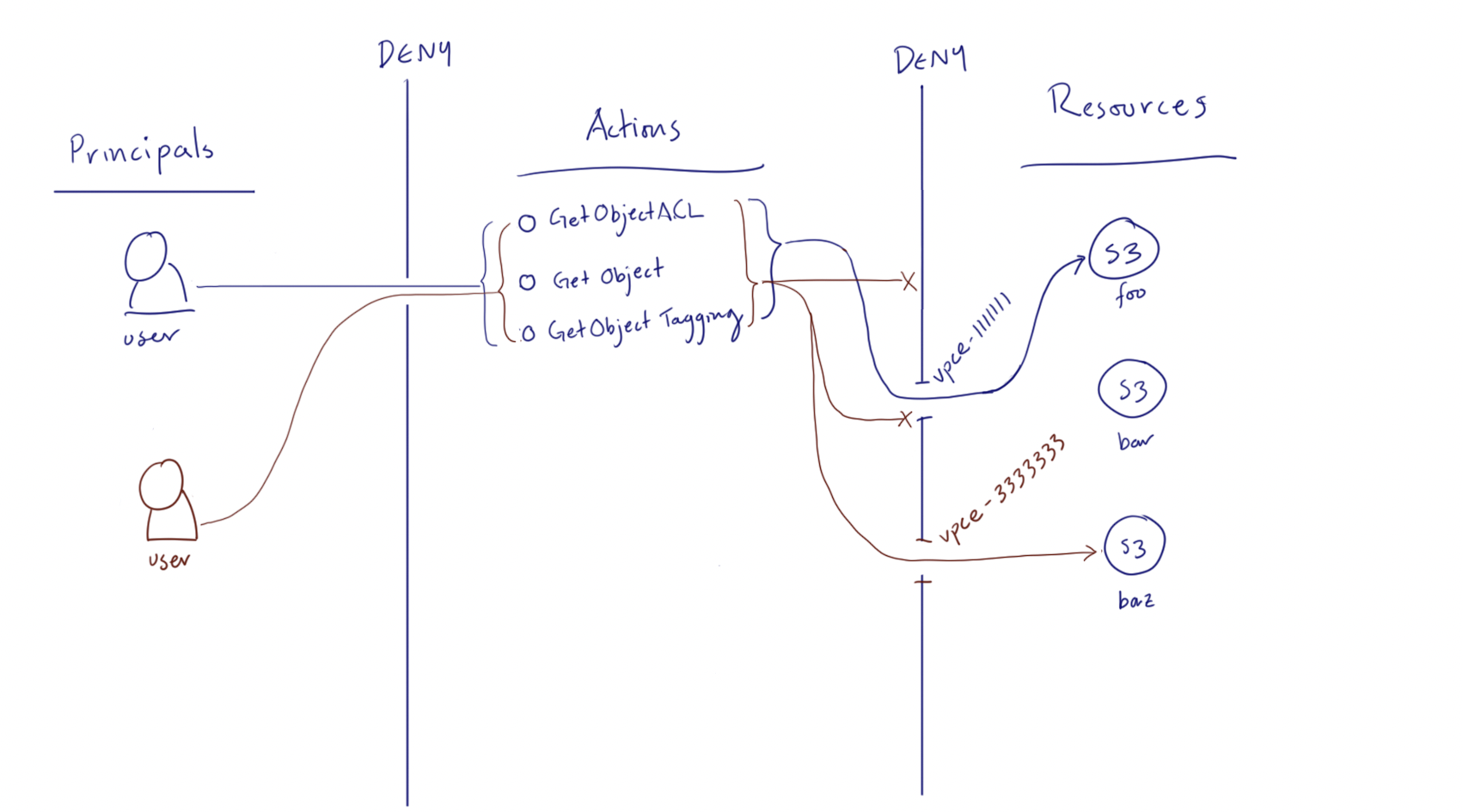
How to scale your authorization needs by using attribute-based access control with S3 | AWS Security Blog

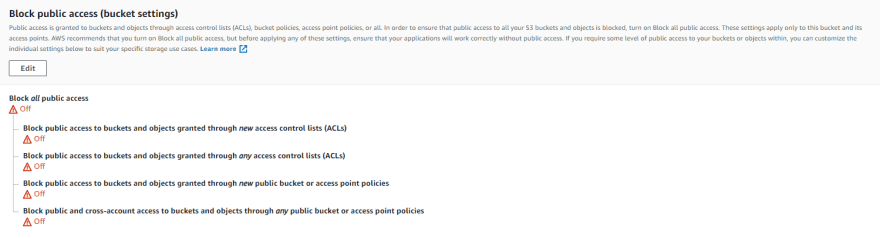
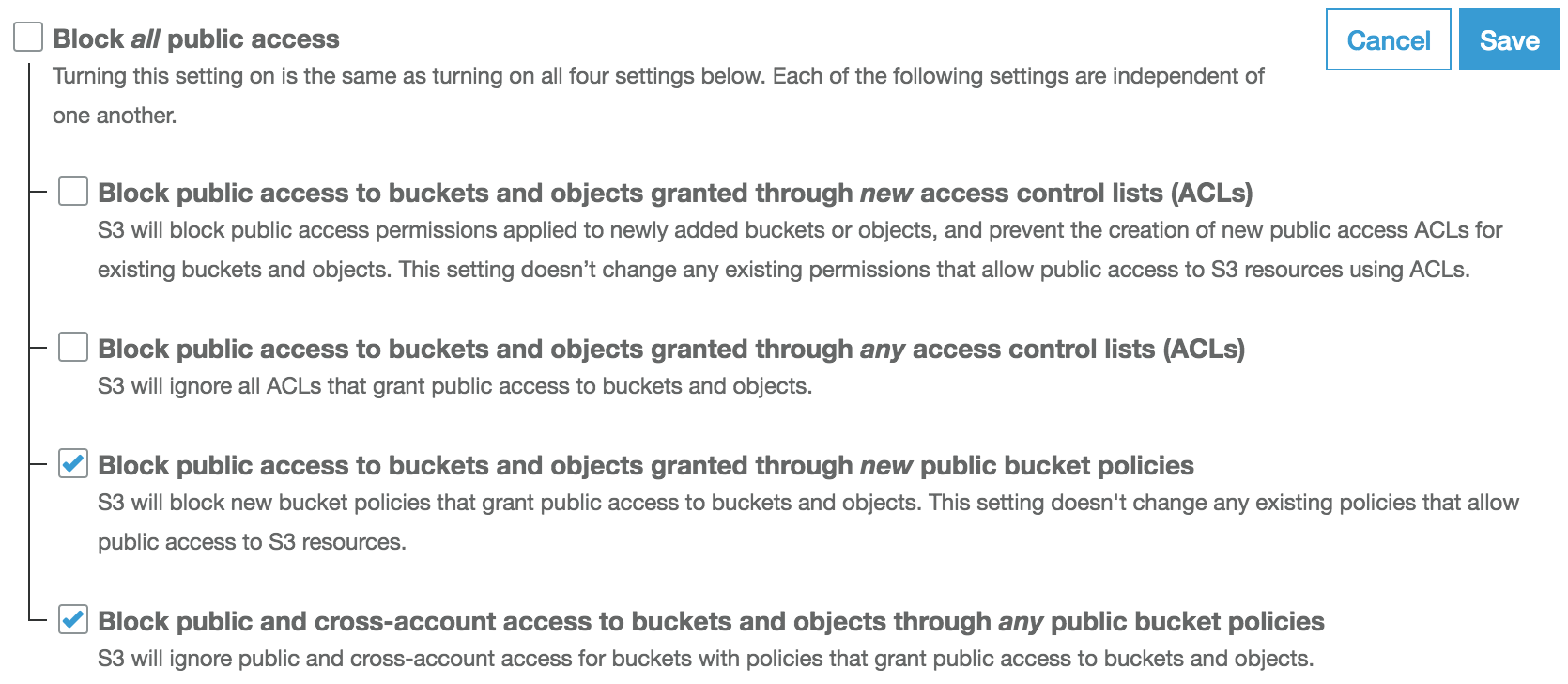
How to Use Bucket Policies and Apply Defense-in-Depth to Help Secure Your Amazon S3 Data | AWS Security Blog
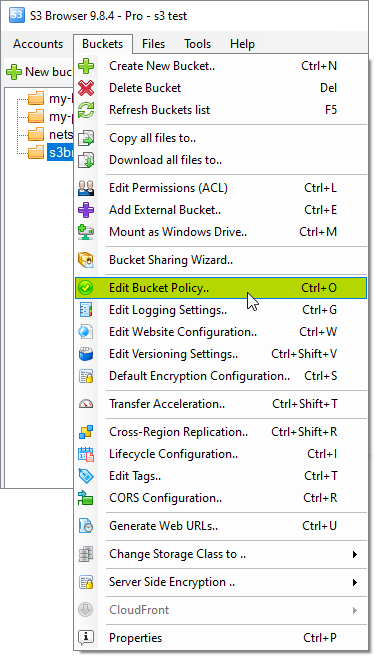
Bucket Sharing Tutorial. How to share Amazon S3 Bucket with another AWS Account. How to grant access to your bucket.

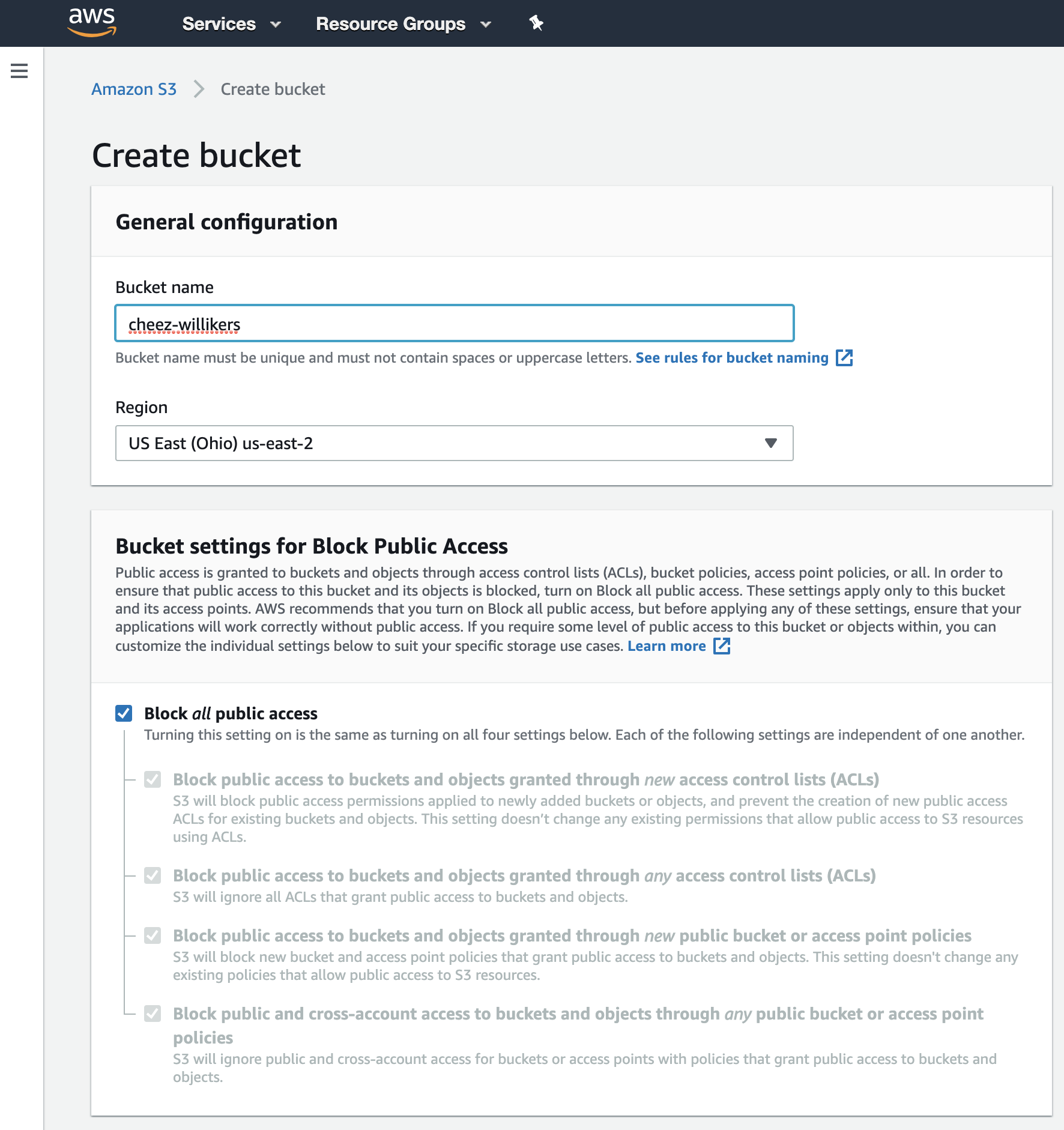
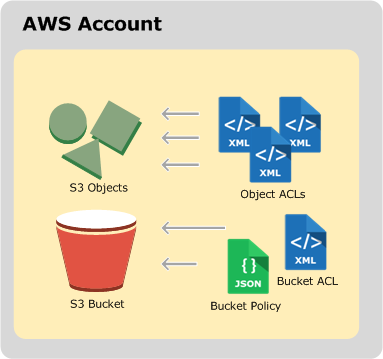
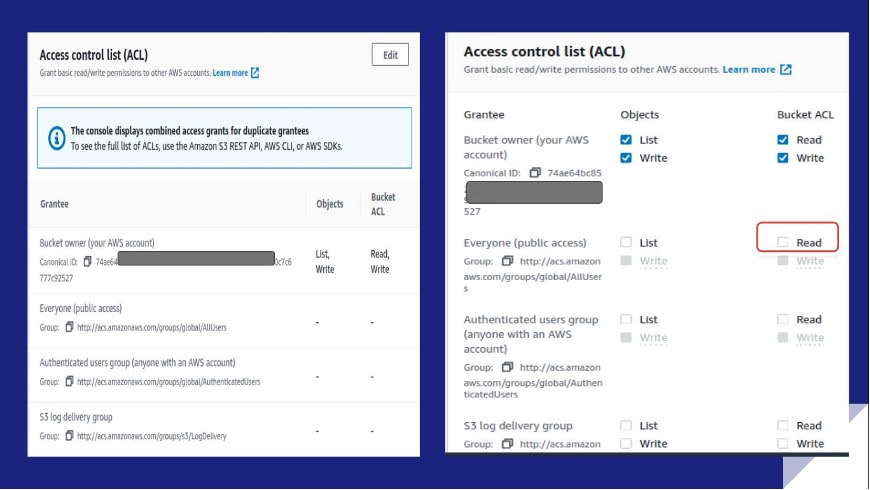
![AWS S3 Bucket Security via Access Control List (ACL) - [Hands on Lab] - YouTube AWS S3 Bucket Security via Access Control List (ACL) - [Hands on Lab] - YouTube](https://i.ytimg.com/vi/NHgdO4cI-Xg/maxresdefault.jpg)