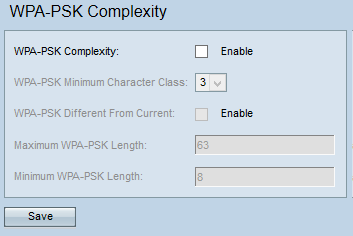
WiFi Protected Access Pre-Shared Key (WPA-PSK) Complexity Configuration on WAP551 and WAP561 Access Points - Cisco
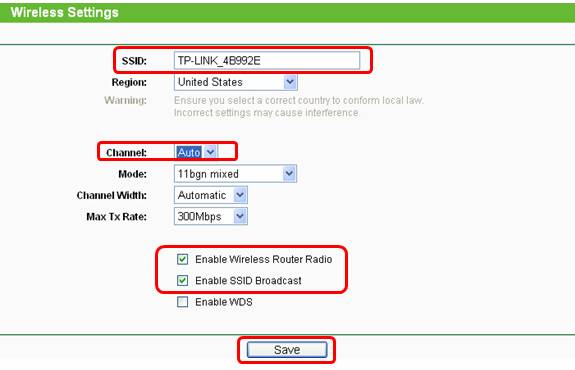
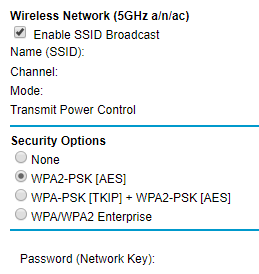
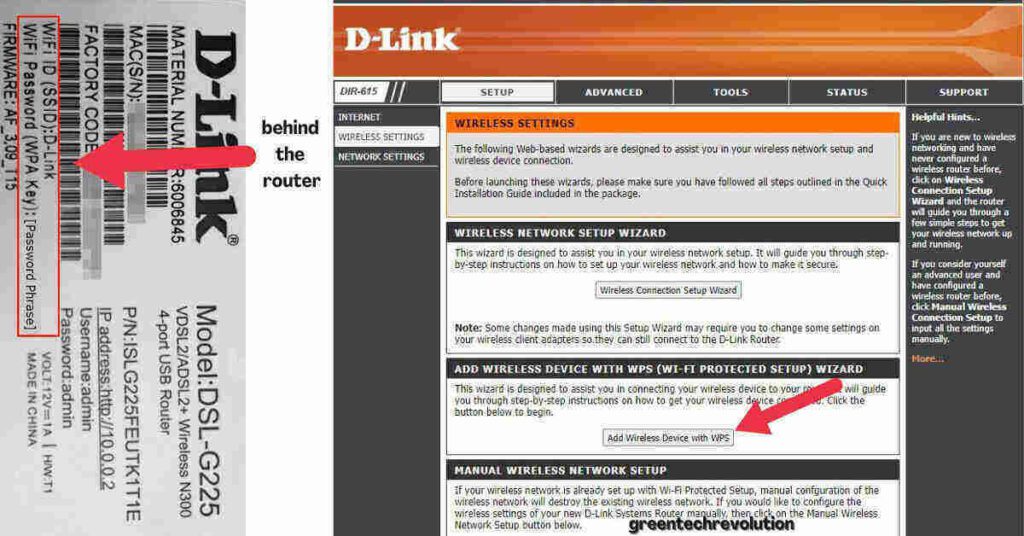
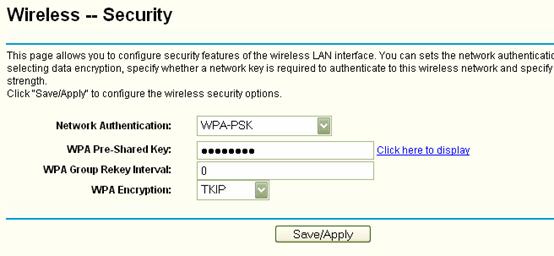
How do I secure/protect my wireless network by using WPA-PSK/WPA2-PSK on TP-Link Wireless 11N Router?
How do I secure/protect my wireless network by using WPA-PSK/WPA2-PSK on TP-Link Wireless 11N Router?

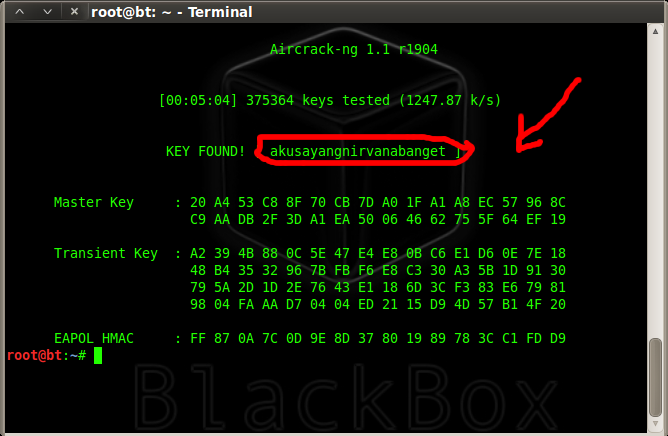
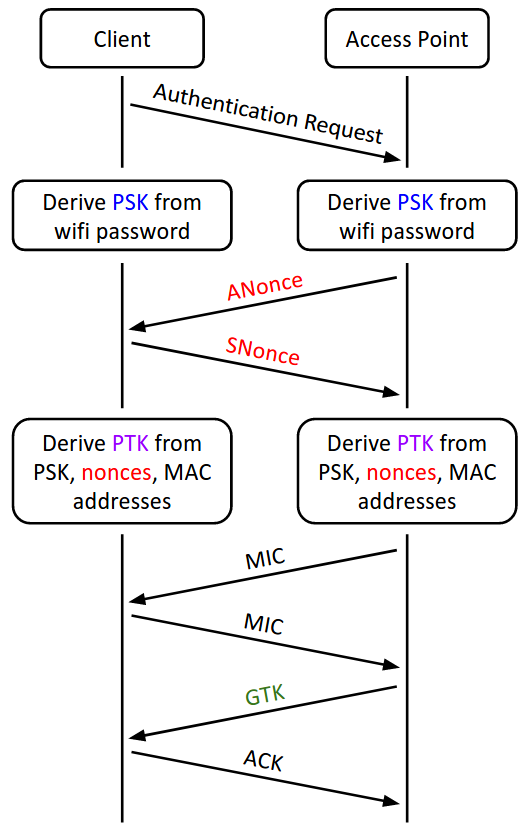
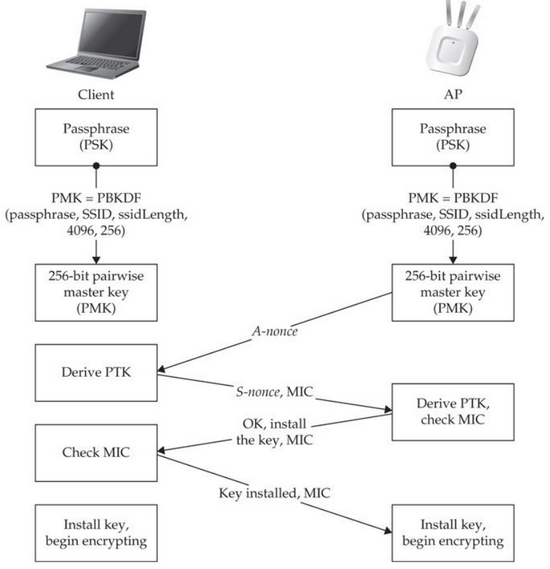
penetration test - can an attacker find WPA2 passphrase given WPA key data and WPA MIC - Information Security Stack Exchange
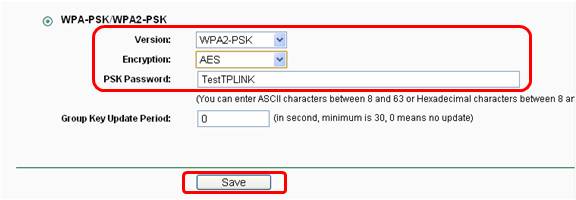
How do I secure/protect my wireless network by using WPA-PSK/WPA2-PSK on TP-Link Wireless 11N Router?





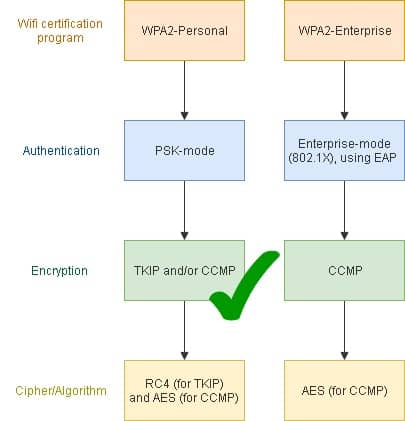
![How to add support for wireless networking WPA2-PSK [AES] on Windows - Super User How to add support for wireless networking WPA2-PSK [AES] on Windows - Super User](https://i.stack.imgur.com/GOXBZ.png)